
Cisco-opplæring
Insoft Services er en av få opplæringsleverandører i EMEAR som tilbyr hele spekteret av Cisco-sertifisering og spesialisert teknologiopplæring.
Les mer
Cisco Sertifisering
Opplev en blandet læringstilnærming som kombinerer det beste av instruktørledet opplæring og e-læring i eget tempo for å hjelpe deg med å forberede deg til sertifiseringseksamen.
Les mer

Cisco Learning Credits
Cisco Learning Credits (CLC) er forhåndsbetalte opplæringskuponger innløst direkte med Cisco som gjør planleggingen for suksessen din enklere når du kjøper Cisco-produkter og -tjenester.
Les mer

Etterutdanning
Cisco Continuing Education Program tilbyr alle aktive sertifiseringsinnehavere fleksible alternativer for å resertifisere ved å fullføre en rekke kvalifiserte opplæringselementer.
Les mer

Cisco Digital Learning
Sertifiserte ansatte er verdsatte eiendeler. Utforsk Ciscos offisielle digitale læringsbibliotek for å utdanne deg gjennom innspilte økter.
Les mer

Cisco Business Enablement
Cisco Business Enablement Partner Program fokuserer på å skjerpe forretningsferdighetene til Cisco Channel Partners og kunder.
Les mer
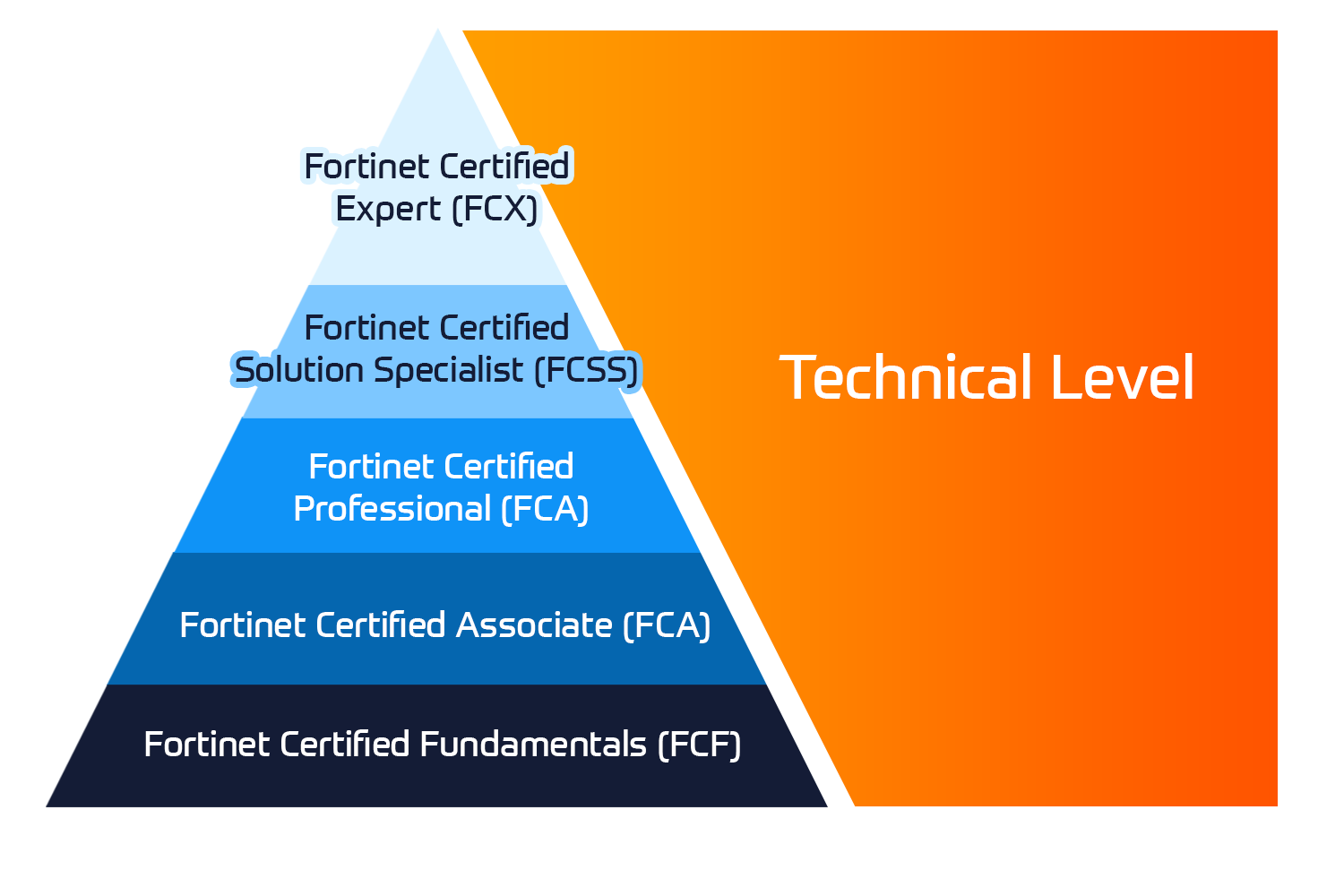
Fortinet Sertifisering
Fortinet Network Security Expert (NSE)-programmet er et opplærings- og sertifiseringsprogram på åtte nivåer for å lære ingeniører om nettverkssikkerheten for Fortinet FW-ferdigheter og -erfaring.
Tekniske kurs

Fortinet-opplæring
Insoft er anerkjent som Fortinet Autorisert Opplæringssenter på utvalgte steder i EMEA.
Les mer

Fortinet opplæringskatalog
Utforsk et bredt utvalg av Fortinet Schedule på tvers av forskjellige land så vel som online kurs.
Les mer
Pakker for Fortinet-tjenester
Insoft Services har utviklet en spesifikk løsning for å effektivisere og forenkle prosessen med å installere eller migrere til Fortinet-produkter.
Les mer

AWS-opplæring
Opplæringen inkluderer laboratorier i eget tempo for praktisk AWS-praksis i virkelige scenarier, slik at du kan lære i ditt eget tempo, i klassen, på jobben eller online.
Tekniske kurs

Løsninger og tjenester
Vi tilbyr innovativ og avansert støtte for design, implementering og optimalisering av IT-løsninger. Vår kundebase inkluderer noen av de største Telcos globalt.
Les mer

Om oss
Insoft Tilbyr autoriserte opplærings- og konsulenttjenester for utvalgte IP-leverandører. Finn ut hvordan vi revolusjonerer bransjen.
Les mer
Contact Us
We would love to hear from you. Please complete this form to pre-book or request further information about our delivery options.

 United Kingdom
United Kingdom Germany
Germany Denmark
Denmark Sweden
Sweden Italy
Italy Netherlands
Netherlands Finland
Finland














 Duration
Duration
 Delivery
Delivery  Price
Price